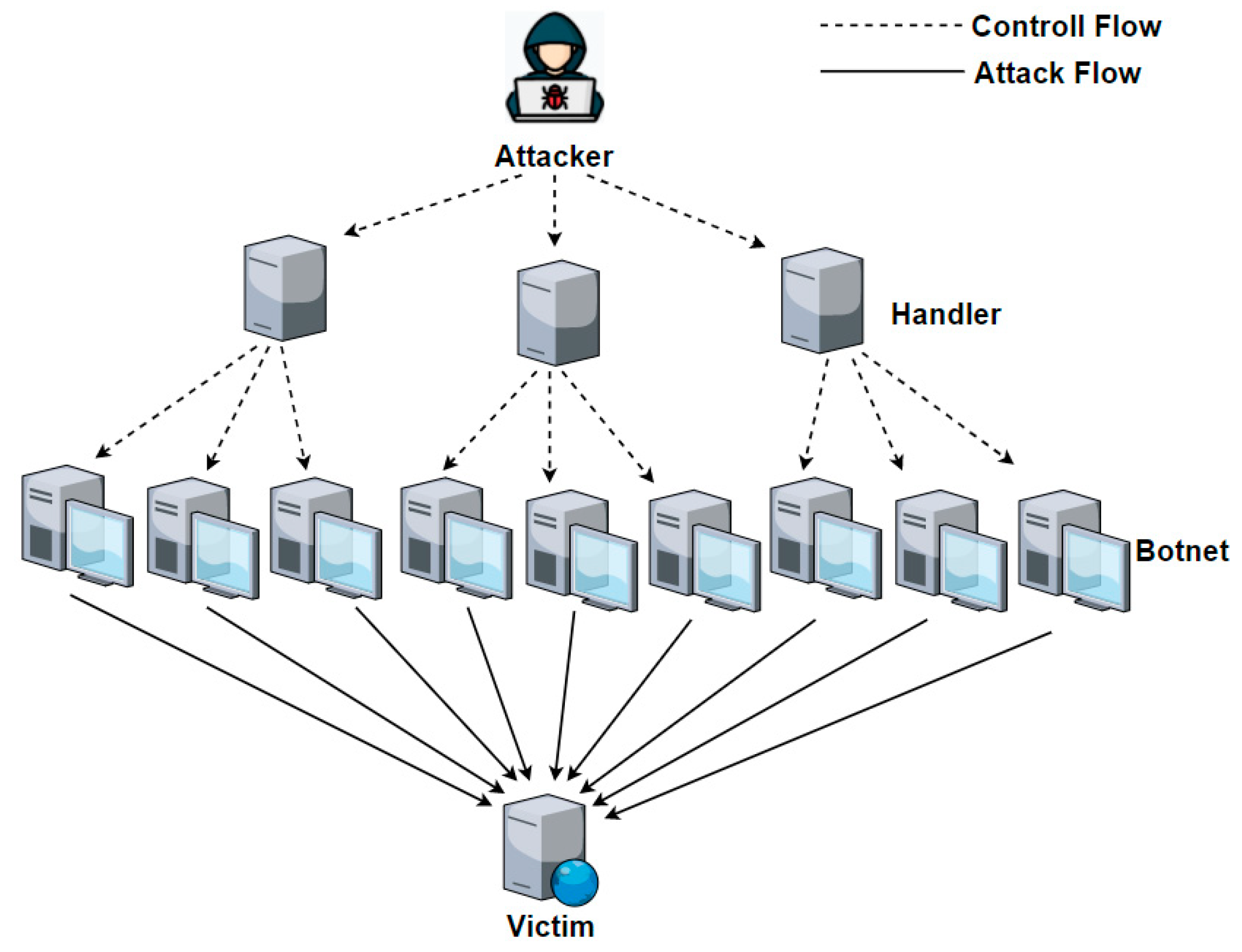
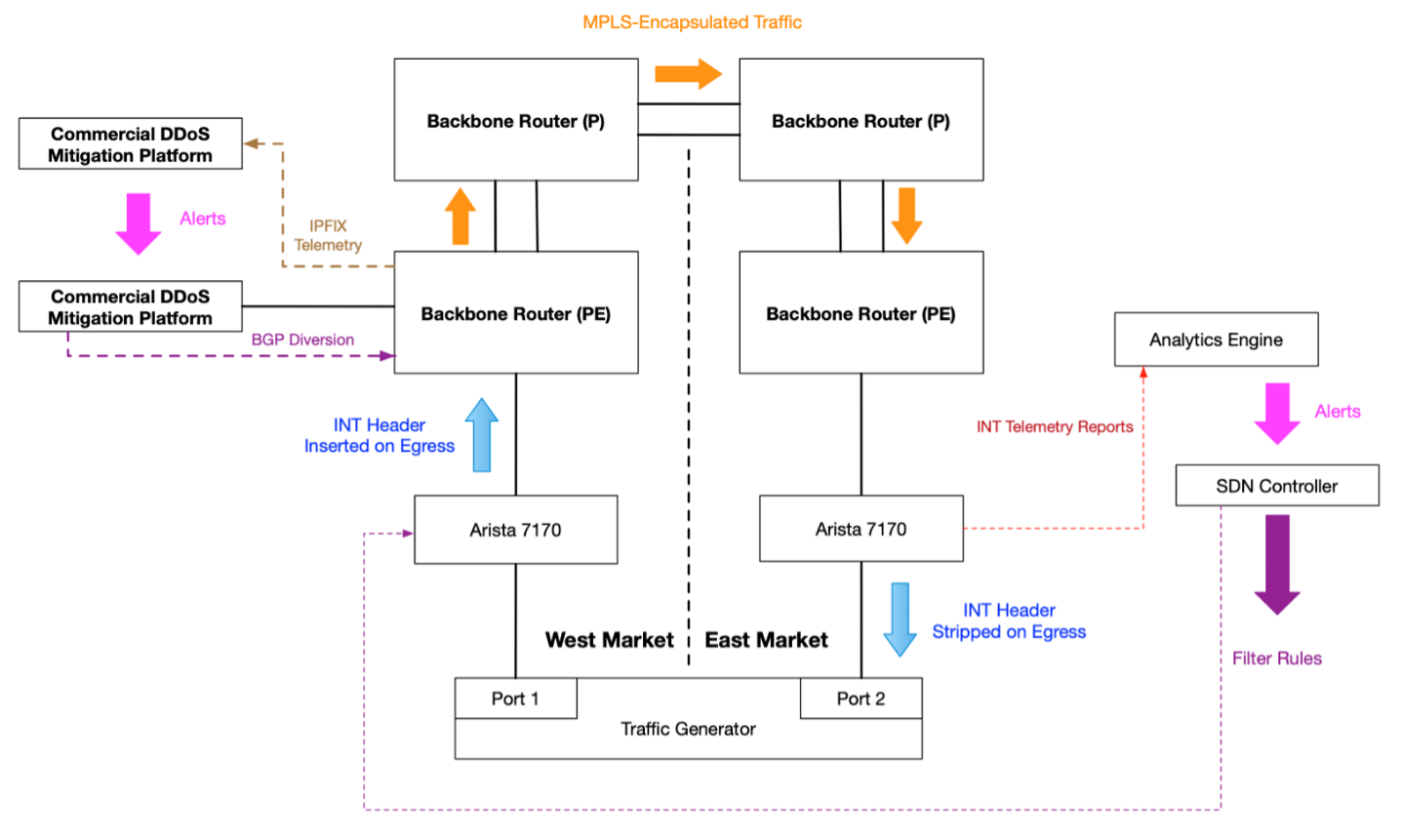
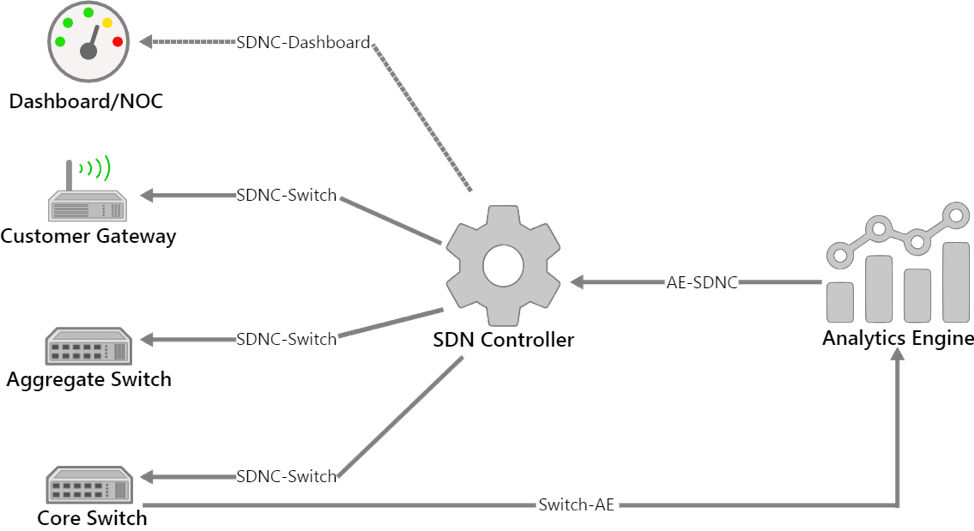
a) SDN/QKD Optical Network testbed. b) DoS attacker for links 1 and 2.... | Download Scientific Diagram
Cyber Attack, Disability and Smile Minimal Line Icons. for Web Application, Printing. Neon Laser 3d Lights. Vector Stock Vector - Illustration of chat, social: 248087457

Typewriter, Cyber attack and Painter minimal line icons. Neon laser 3d lights. Accounting report icons. For web, application, printing. Writer machine, Web ddos, Paint brush. Check finance. Vector Stock Vector | Adobe

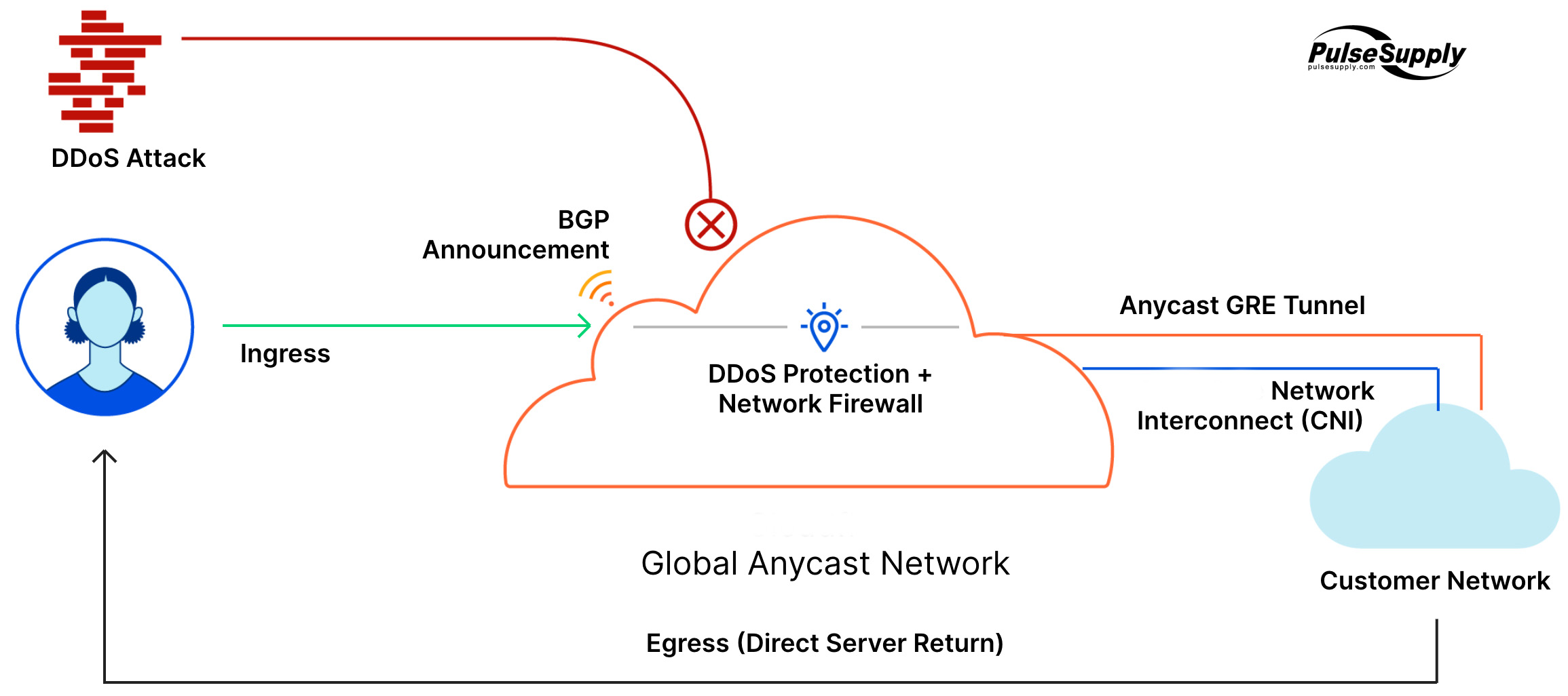
Ashley Stephenson on LinkedIn: What do these Tier 1, Tier 2 and Tier 3 Service Providers have in common?…
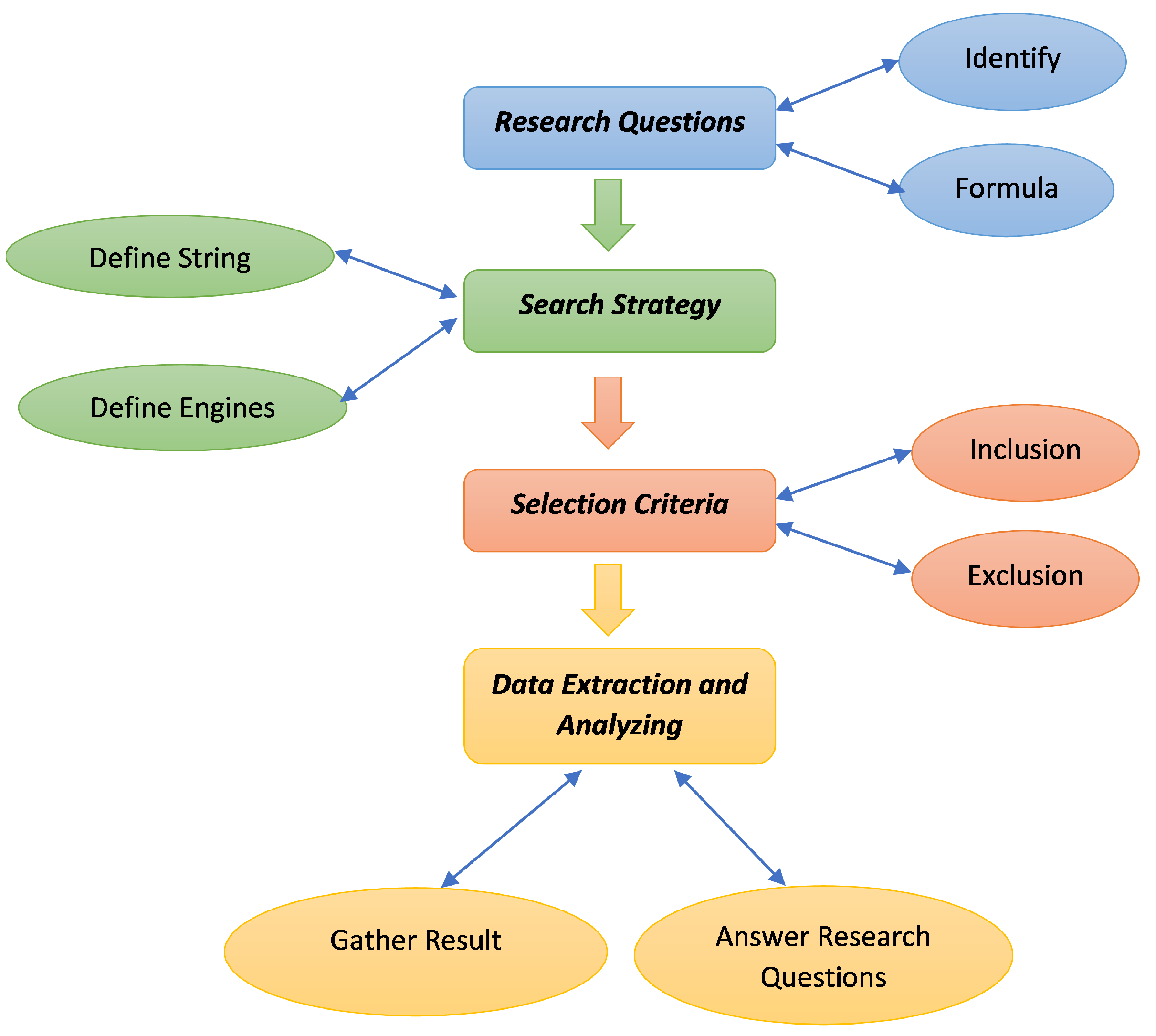
Applied Sciences | Free Full-Text | Machine Learning Techniques to Detect a DDoS Attack in SDN: A Systematic Review